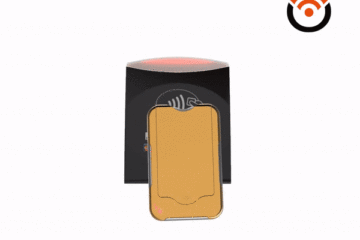
RFID Cloaked is a private limited company based in Exeter, Devon. Established in the South West of England in 2015, we manufacture and supply RFID blocking cards for ID cards, contactless payment credit and debit cards. We also supply our material as NFC and electromagnetic shielding film/ fabrics.
Our shielding films protect against radio frequencies: such as Bluetooth, Wifi, RFID and NFC, 3 and 4G mobile phone signals
We protect and secure ID cards (Identification) and payment cards from being hacked, skimmed and cloned from the most powerful RFID and NFC readers for frequencies of 13.56Mhz and 125Khz.
We have new products under development for full shielding of passports and mobile phones for example.
If you require any further information please contact us.