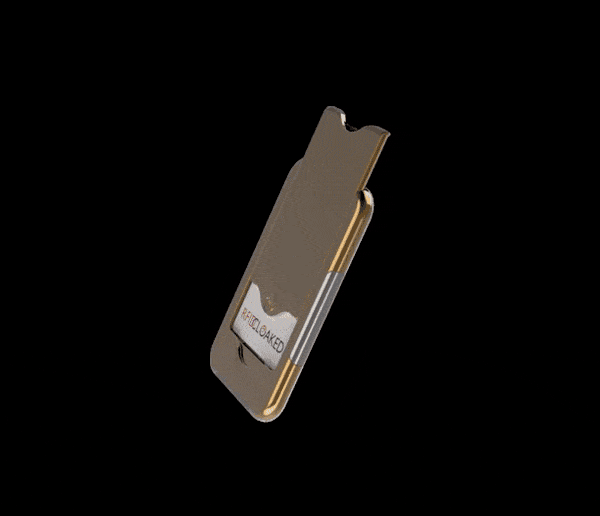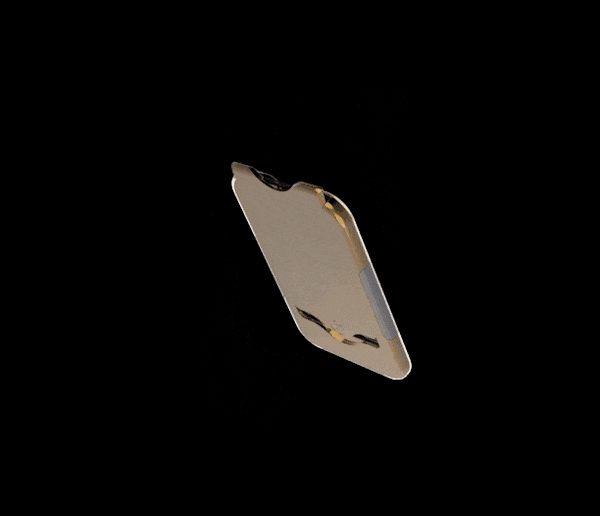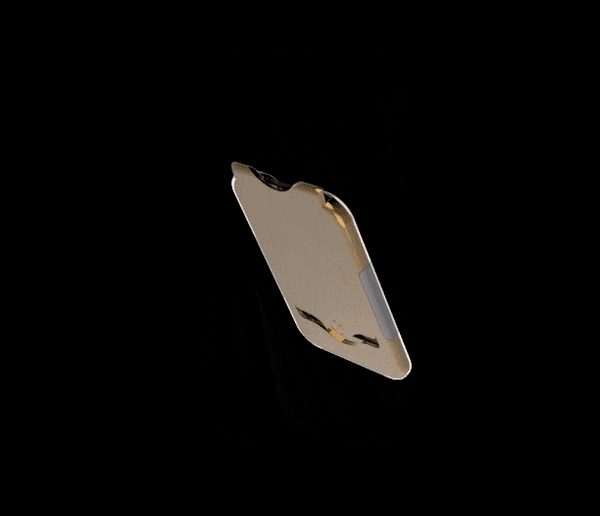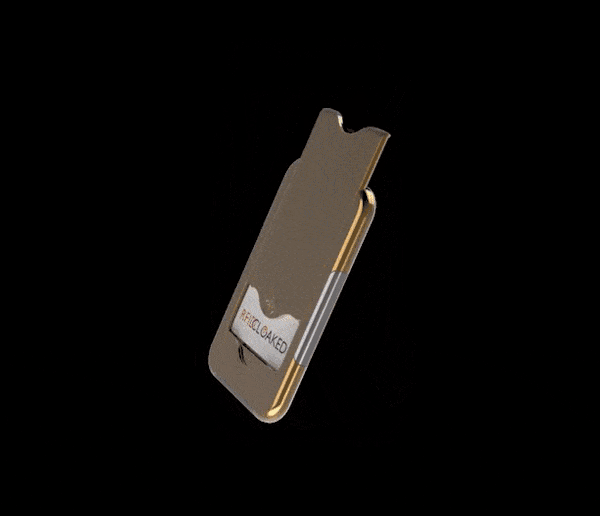
Can someone steal your credit card info from your pocket?
Can someone steal your credit card info from your pocket? Yes, if you have a contactless card with an RFID chip, the data can be read from it. What can help steal your credit card info? Contactless payment cards have …